Trustlook's Integration with OKC (OKX Chain)
San Jose, California, Oct. 19, 2022, Trustlook, the global leader ...


On May 3, 26.7 million TRX was taken away by an attacker “wojak” (discord name, address: THeRTTCvN4SHEVYNqcLVLNGGVsWLR4smyH). These TRX tokens worth around 700K USD at that moment. This is the second big security event from TronBank team since the huge BTTBank BTT token stolen event. The reason for the stolen this time is because of a backdoor someone set up in the withdraw function of the smart contract.
According to what Tronbank team’s statement, they were trying to compiled the smart contract and verified it on TSC (TronSmartContract.space) for many times but ended up with failures. So they used TSC to compile and deploy and somehow the backdoor was injected by Khanh (Author of https://tronsmartcontract.space/#/author, Tron address:TTX5N2wxLeyWBSNE6UeaBjCFZbpa2FH6jr).
The above statement was from the post here.
Apparently, after the smart contract was deployed the compiled bytecode was not human friendly and hard to inspect without any reverse engining tools. The backdoor was added into the smart contract function withdraw(). By using our online decompiling tool, we can easily found the the backdoor code:
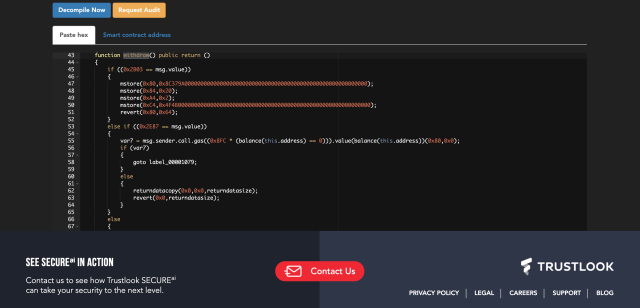
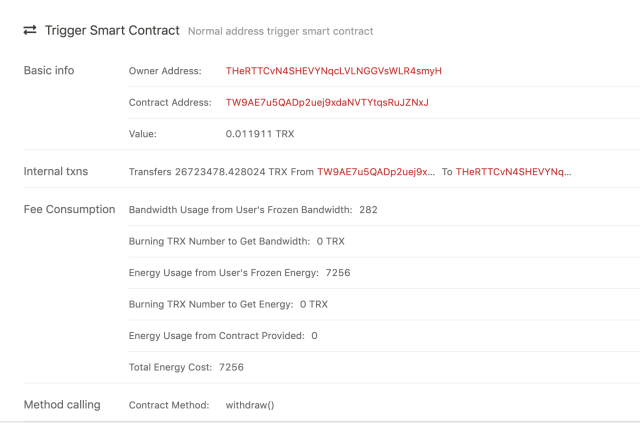
From above photo snapshot, we can clearly see when the msg.value is 0x2E87 (11911) the smart contract will send all balance of the contract to the sender. Therefore the attacker wojak transferred all TRX to his own address by calling withdraw function with value of 0.011911 TRX:
One interesting part of the story is after the attack occurred, this wojak claimed in the discord channel that he didn’t realize the transfer of the tokens until later review and he was originally testing his program on all smart contract on Tronbank network.
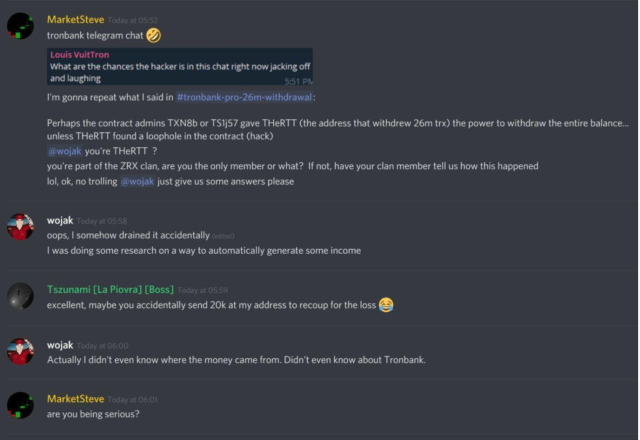
He also stated he will refund all tokens to the original investors but ended up with disappearance.
One lesson we can learn from this attack is that the security issue inside block chain ecosystem is never an adversary or a patch anymore. It means real finance loss for investors or users. Also, since the smart contract’s final format is for Virtual Machine and not human, we should really aware of the real logic in the bytecode and not the source code. Especially, the binary was not compiled by your own compilers. Even the bytecode is not meant to be read by human, but with help of de-compiler tool like Smart Contract Guardian, the logic of the bytecode can still by retrieved clearly. We also offer bytecode level smart contract audit service to make sure all your contract is safe and operate in the logic that is supposed to be.