
如果你是一个安卓应用的开发者,那么你一定对热更新的概念有所了解,甚至你的应用中也采用了某种热更新技术。热更新技术在几年前就被人提出,自然是有其市场诉求。当一个应用发布之后,开发者突然发现了一个严重bug需要紧急修复,然而从代码修改测试,联系应用商店更新,用户下载更新,需要一个很繁琐的流程。然后对于bug自身的修改也许只是一行代码或一个变量的调整。面对这样的情况,安卓的开发者开始寻求简单快捷的更新方式,热补丁技术应运而生。随着最开始的Dexposed,Q-zone超级补丁,Andfix,到现在的Tinker,Sophix,热补丁技术在这些年也有了很多的改进和完善。之前也会很多非常好的文章介绍常见的热补丁技术。在这里非常推荐Sophix团队人员出版的《Android热修复技术原理》一书。其他优秀的介绍文章也会在参考文献中列出。从技术实现来看,热补丁通常可以采用Native的方式,和Java层面进行热更新。 Java 层:通过动态加载代码和资源来实现。 Native

In recent years, there have been many data breach events even from some very well-known enterprises, and the security of personal privacy has been attracting people's attention more and more. How to effectively

Author: Yue LuoTranslated by c0zzySummaryThe ransomware is more disguised as some system function components, or some special function APP (such as porn, game plug-in, cracked applications, etc.), to trick users into installing, after

作者:月落前言勒索软件多伪装成一些系统功能组件,或一些特殊功能的APP(如色情、游戏外挂、正规应用破解版等),诱骗用户进行安装,在索要系统的一些权限之后,锁定用户的设备,并进行敲诈。多数勒索软件由于自身的设计或bug,以及高版本安卓系统上API的限制,即便用户交了赎金也无法成功解锁,这将直接导致数据的丢失,个人信息的泄露,甚至信用卡被盗刷,对用户造成了极大的损失。调查通过一系列的样本研究与受害者反馈,得知勒索软件通常有两种类型:锁屏类文件加密类索要赎金的形式包括但不限于:支付宝/微信转账、比特币交易、索要信用卡信息。工作原理索要设备管理器权限 Device admin是一个很危险的权限,设计之初,这个功能是用于厂家开发手机防盗功能的一个接口,只要用户安装此类APP并点击Activate,APP便具备设备管理员权限,并具备以下权限的一种或多种:加密存储禁用照相机禁用锁屏相关特性强制密码过期锁定屏幕限制可用密码类型重置密码监控密码输入的正确或错误擦除数据一旦给予了恶意应用如上权限,
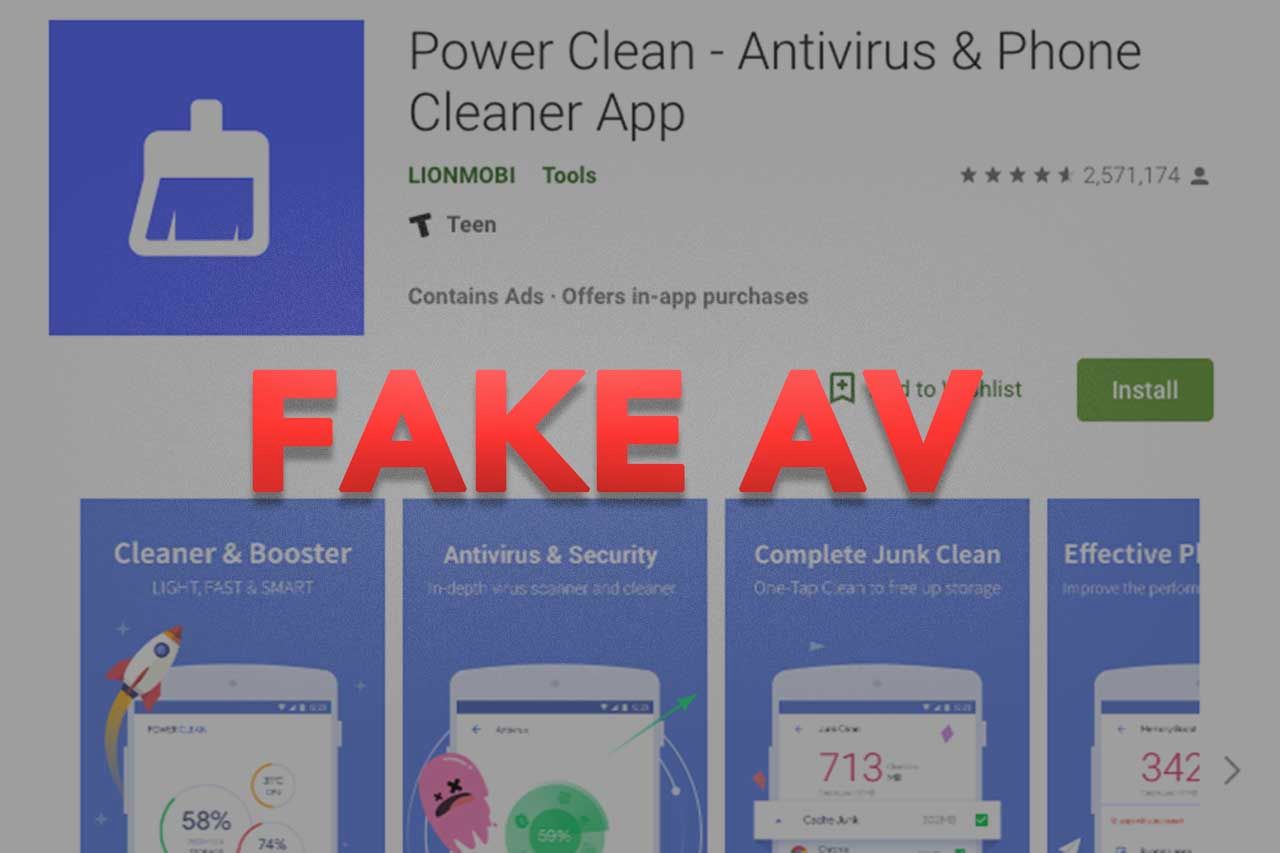
由于Android生态系统对用户更加开放,因此你可以从许多来源下载和安装任何应用程序,而不仅仅是谷歌应用商店。但是,App开发人员和恶意软件作者也获得了同样的便利。安全问题始终是Android用户关心的一个重要话题,特别是对于中国用户。出于这个原因,市场上有很多针对Android发布的安全应用程序。在本系列中,我们将通过测试分析一些知名的安全移动应用程序,让非技术用户来了解它们真正的性能表现。让我们先从Play商店中一个非常受欢迎的应用程序开始:来自Lionmobi的Power Clean - Antivirus&Phone Cleaner App。在谷歌应用商店,你可以看到几款来自Lionmobi公司的安全和工具类应用,我们测试分析了其中所有和安全相关的应用。但是在这篇文章中我们重点关注Power Clean这个应用,因为这个应用基本包含了其他几个应用的主要功能。对于同一功能在其他应用上的性能表现是类似的,其中的代码也有很多重复。Power Clean自身拥有超过1亿下载量,从显示数据上看目前仍有超过250万活跃用户。除了此应用程序的流行程度之外,我们关注此应用程序的另一个原因是它具有非常多的安全和工具类功能,
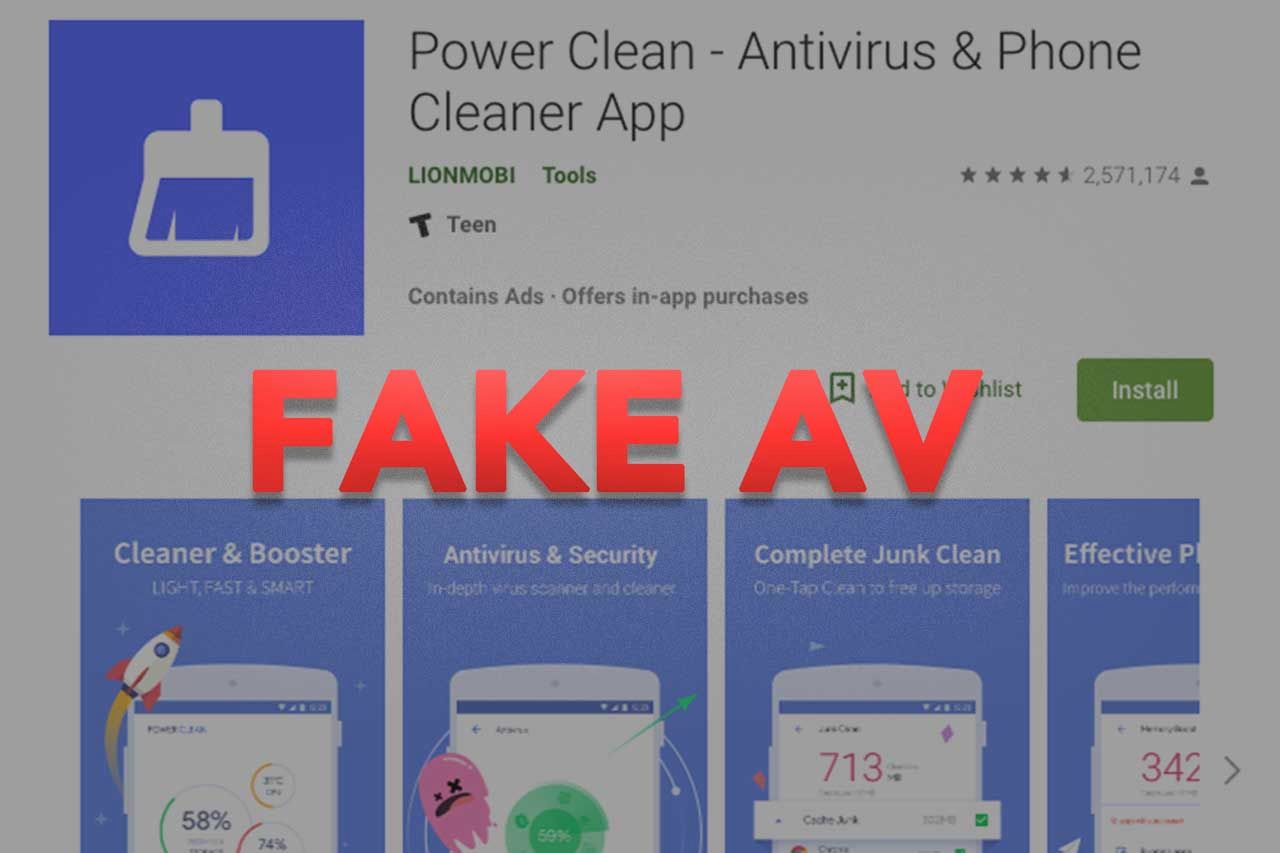
An Anti-Virus mobile App can have fancy UI and claimed to have a lot of protections to your phone. However, non-tech users wouldn't know whether it is true or not. Let's have some reviews on some popular mobile security Apps.

On May 3, 26.7 million TRX was taken away by an attacker “wojak” (discord name, address: THeRTTCvN4SHEVYNqcLVLNGGVsWLR4smyH). These TRX tokens worth around 700K USD at that moment. This is the second big

Since I started working in the Ethereum ecosystem and auditing Ethereum smart contract in bytecode format. I have evaluated many well-known projects which claimed they can decompile EVM (Ethereum Virtual Machine) bytecode. However,

In previous section:Understand EVM bytecode – Part 1Understand EVM bytecode – Part 2Understand EVM bytecode – Part 3We have talked about how different Solidity data types are implemented in storage. For this section we will

In previous sections:Understand EVM bytecode – Part 1Understand EVM bytecode – Part 2We have talked about creation and runtime parts of the EVM bytecode. We have seen that the stack variables are commonly used

In the first section,Understand EVM bytecode – Part 1We have inspected the contract creation part of the EVM bytecode of the smart contract. In this section we will analyze the runtime EVM bytecode.

If you have started reading this article, I guess you already know what EVM stands for. So I wouldn’t spend too much time on the background of Ethereum. If you do need












