Trustlook's Integration with OKC (OKX Chain)
San Jose, California, Oct. 19, 2022, Trustlook, the global leader ...


Trustlook has released a scanner and vaccine toolkit to help system administrators protect Windows computers that are either vulnerable to or have been infected with the dangerous strain of ransomware known as WannaCry. The toolkit can be found on GitHub.
Banks, telephone companies and hospitals have all been ensnared in this worldwide hack, with the malware locking down computers while demanding a hefty sum for freedom. The attack has hit more than 230,000 computers in 150 countries including China, Russia, Spain, Italy and Vietnam, with hospitals in the UK attracting the most attention because real lives have been put at risk while their devices are locked down. Ransom payments have been demanded in the cryptocurrency bitcoin in 28 languages.
Trustlook Labs has tracked the global wave of WannaCry attacks. The malware exploits the vulnerability identified CVE-2017-0145 (Windows SMB Remote Code Execution vulnerability) to spread itself. The malware uses the publicly available “Eternal Blue exploit” by the hacker group “The Shadow Brokers.” The vulnerability exists in unpatched versions of newer Windows operating system, as well as unsupported versions of Windows XP, 2003 and 8.
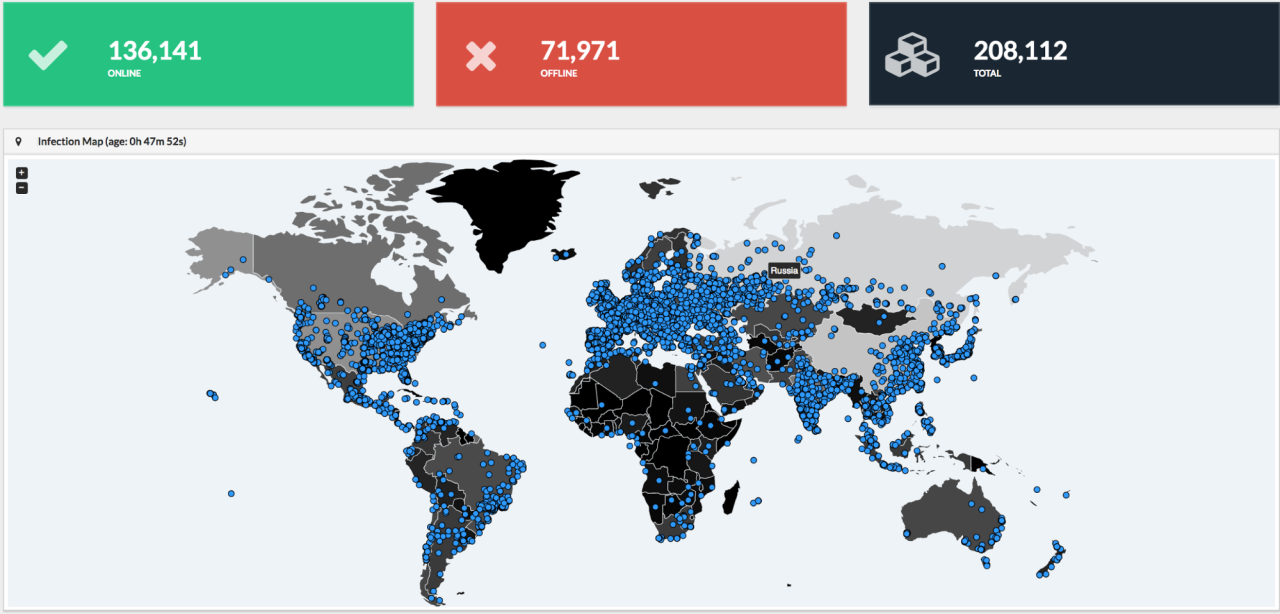
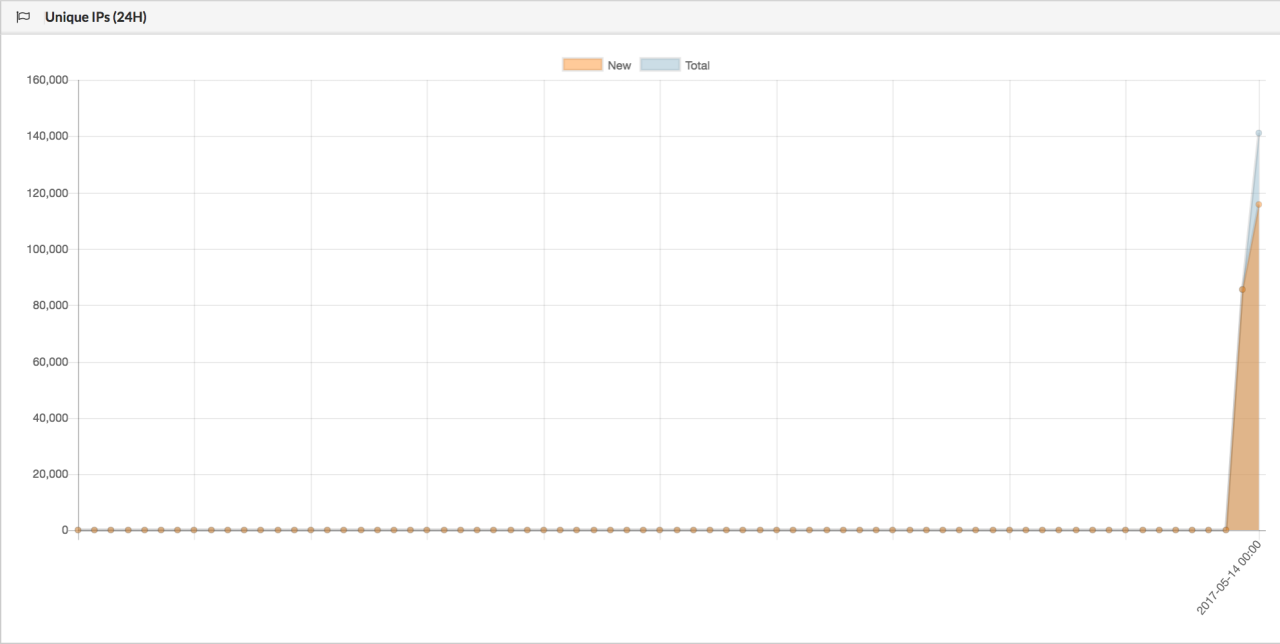
The following images are a tracker map and the number of unique IP addresses infected over the last 24 hours.
The WannaCry malware comes as a dropper with two components:
B.WNRY: A BMP FILE USED TO DISPLAY THE RANSOME MESSAGET.WNRY: ENCRYPTED FILE WITH “WANACRY!” HEADER, DECRYPTED TO A DLL MODULE WHICH IS THE MAIN PAYLOAD.C.WNRY: CONFIGURATION FILE. CONTAINS SEVERAL TOR SERVER ADDRESS AND LINK FOR TOR BROWSER.S.WNRY: ZIP COMPONENT FILER.WNRY: RANSOMWARE Q&AU.WNRY: DECRYPTOR EXECUTABLETASKDL.EXE: EXECUTABLE USED TO DELETE FILETASKSE.EXE: APPLICATION TO START A REMOTE SESSIONMSG/M_.WNRY: LOCALIZED LANGUAGE FILES
If the malware starts with parameter “/i”, it copies itself into:
“C:\PROGRAMDATA\<RANDOM CHARACTERS>\TASKSCHE.EXE” AND CREATES SERVICE “<RANDOM CHARACTERS>”, THE SERVICE’S BINARYPATHNAME “CMD.EXE /C “C:\PROGRAMDATA\<RANDOM CHARACTERS>\TASKSCHE.EXE”
The malware creates a mutex to make sure only one instance is running in the system. In this version of the malware (2.0) the mutex is:
“GLOBAL\\MSWINZONESCACHECOUNTERMUTEXA0”. ANOTHER VERSION OF MALWARE (1.) USES MUTEX “GLOBAL\\WINDOWS_TASKCST_MUTEX”.
The malware runs “icacls . /grant Everyone:F /T /C /Q” to grant access to all users on the system.
The malware then decrypts the payload DLL module into memory and calls the export function “TaskStart”. The malware generates a 2048 bit RSA key by calling the “CryptGenKey” function.
The malware then exports a public key and a private key. The public key is saved as “000000000.pky”. The private key is then encrypted by using another public key, which exists in the binary and is saved as “00000000.eky”. The related private key is held by the malware writer. The malware emulates the system and searches for the file with the following extensions:
.123, .JPEG , .RB , .602 , .JPG , .RTF , .DOC , .JS , .SCH , .3DM , .JSP , .SH , .3DS , .KEY , .SLDM , .3G2 , .LAY , .SLDM , .3GP , .LAY6 , .SLDX , .7Z , .LDF , .SLK , .ACCDB , .M3U , .SLN , .AES , .M4U , .SNT , .AI , .MAX , .SQL , .ARC , .MDB , .SQLITE3 , .ASC , .MDF , .SQLITEDB , .ASF , .MID , .STC , .ASM , .MKV , .STD , .ASP , .MML , .STI , .AVI , .MOV , .STW , .BACKUP , .MP3 , .SUO , .BAK , .MP4 , .SVG , .BAT , .MPEG , .SWF , .BMP , .MPG , .SXC , .BRD , .MSG , .SXD , .BZ2 , .MYD , .SXI , .C , .MYI , .SXM , .CGM , .NEF , .SXW , .CLASS , .ODB , .TAR , .CMD , .ODG , .TBK , .CPP , .ODP , .TGZ , .CRT , .ODS , .TIF , .CS , .ODT , .TIFF , .CSR , .ONETOC2 , .TXT , .CSV , .OST , .UOP , .DB , .OTG , .UOT , .DBF , .OTP , .VB , .DCH , .OTS , .VBS , .DER” , .OTT , .VCD , .DIF , .P12 , .VDI , .DIP , .PAQ , .VMDK , .DJVU , .PAS , .VMX , .DOCB , .PDF , .VOB , .DOCM , .PEM , .VSD , .DOCX , .PFX , .VSDX , .DOT , .PHP , .WAV , .DOTM , .PL , .WB2 , .DOTX , .PNG , .WK1 , .DWG , .POT , .WKS , .EDB , .POTM , .WMA , .EML , .POTX , .WMV , .FLA , .PPAM , .XLC , .FLV , .PPS , .XLM , .FRM , .PPSM , .XLS , .GIF , .PPSX , .XLSB , .GPG , .PPT , .XLSM , .GZ , .PPTM , .XLSX , .H , .PPTX , .XLT , .HWP , .PS1 , .XLTM , .IBD , .PSD , .XLTX , .ISO , .PST , .XLW , .JAR , .RAR , .ZIP , .JAVA , .RAW.
Once the file is found, the malware call “CryptGenRandom” to create a random key, then uses the aforementioned generated public key to encrypt it. This key is used to encrypt the file, and the key itself is written into the file. A header string “WANACRY!” is written into the file as a flag to make sure the file is encrypted. The encrypted file is appended with a “.WNCRYT” file extension.
The malware runs the following commands to delete the system shadow copies:
CMD.EXE /C VSSADMIN DELETE SHADOWS /ALL /QUIET & WMIC SHADOWCOPY DELETE & BCDEDIT /SET {DEFAULT} BOOTSTATUSPOLICY IGNOREALLFAILURES & BCDEDIT /SET {DEFAULT} RECOVERYENABLED NO & WBADMIN DELETE CATALOG –QUIET
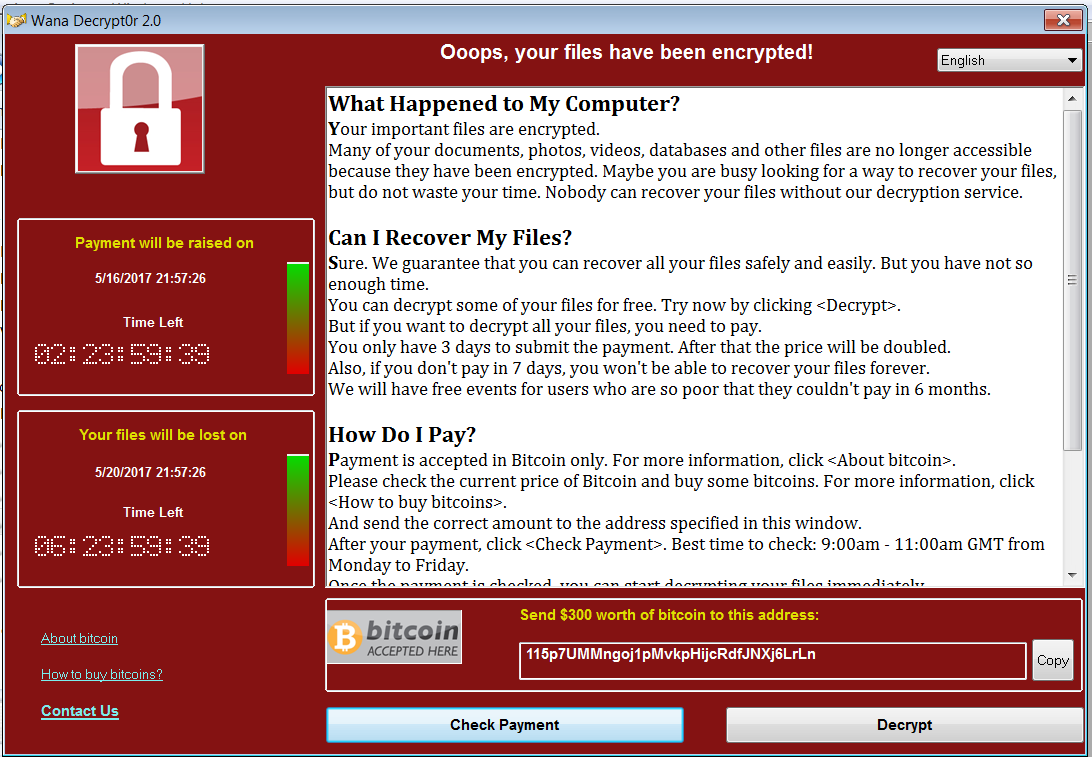
The malware then displays the following ransom note:
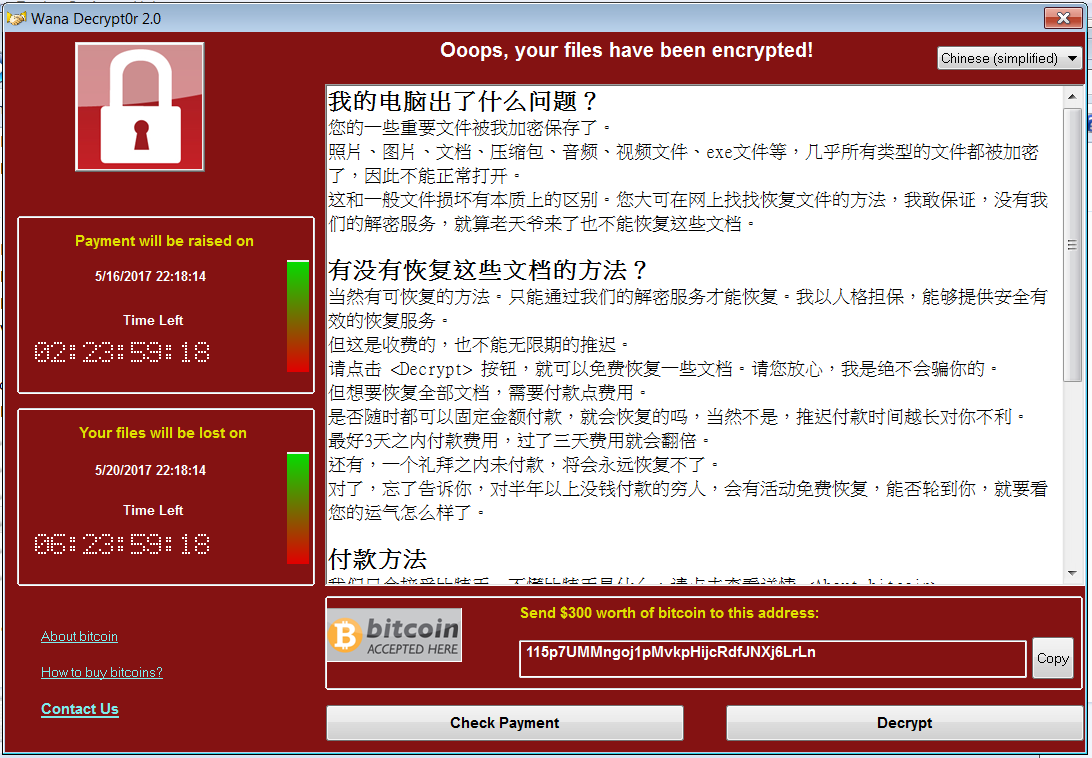
The user can select a different language:
The malware runs a decryptor application to check if the user has paid the ransom. If so, the “.eky” file is sent to the server and decrypts the files by using the private key held by the writer. The decrypted key is then used to decrypt the file.
Trustlook has released a Wannacry Scanner to help system admin scan their network for vulnerable windows systems.
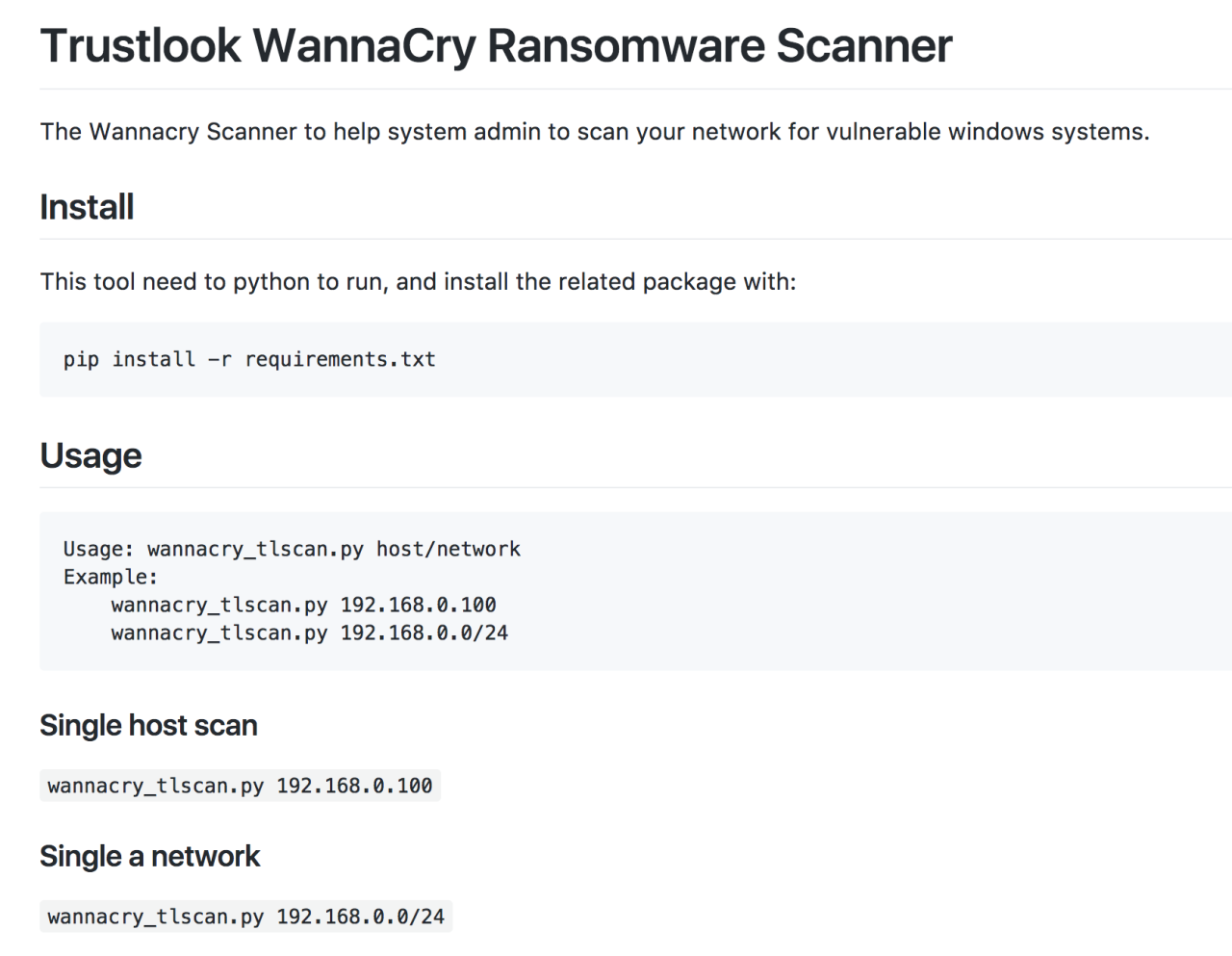
WannaCry Scanner Download Link
https://github.com/apkjet/TrustlookWannaCryToolkit/tree/master/scanner
Here is an screen capture of the tool:
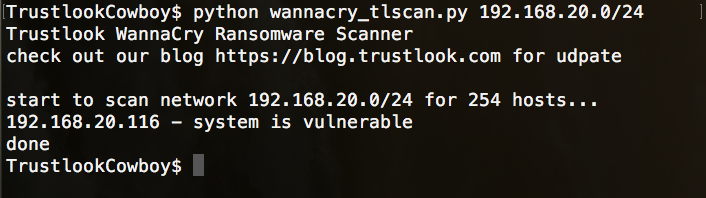
Trustlook’s WannaCry Ransomware Vaccine tool does not require a system reboot. Just run this tool or add it to your windows startup script to help you block the ransomware attack.
Screenshot for WannaCry Ransomware Vaccine Tool (Vaccine for both version 1 and version 2)
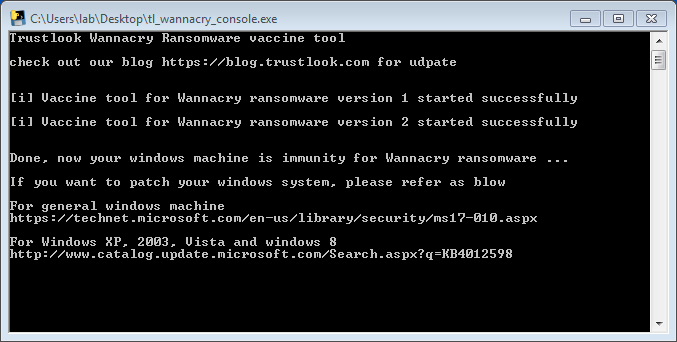
Trustlook WannaCry Ransomware vaccine tool download link:
https://github.com/apkjet/TrustlookWannaCryToolkit/tree/master/vaccine
As of this writing, Trustlook has collected 49 different WannaCry samples. Each sample has been tested by Trustlook, and each has been detected and safely vaccinated.
Below are the SHA256 hashes related to this ransomware:
dff26a9a44baa3ce109b8df41ae0a301d9e4a28ad7bd7721bbb7ccd137bfd69600fdb4c1c49aef198f37b8061eb585b8f9a4d5e6c62251441831fe2f6a0a25b7043e0d0d8b8cda56851f5b853f244f677bd1fd50f869075ef7ba1110771f70c209a46b3e1be080745a6d8d88d6b5bd351b1c7586ae0dc94d0c238ee36421cafa11011a590796f6c52b046262f2f60694310fa71441363d9116ada7248e58509a11d0f63c06263f50b972287b4bbd1abe0089bc993f73d75768b6b41e3d6f6d4916493ecc4c4bc5746acbe96bd8af001f733114070d694db76ea7b5a0de7ad0ab190d9c3e071a38cb26211bfffeb6c4bb88bd74c6bf99db9bb1f084c6a7e1df4e201f42080e1c989774d05d5b127a8cd4b4781f1956b78df7c01112436c89b2c922ccdf145e5792a22ad6349aba37d960db77af7e0b6cae826d228b824670509224d004a104d4d54034dbcffc2a4b19a11f39008a575aa614ea04703480b1022c2584e1521065e45ec3c17767c065429038fc6291c091097ea8b22c8a502c41dd2ca2d550e603d74dedda03156023135b38da3630cb014e3d00b1263358c5f00d3f3a9dde96ec4107f67b0559b4e95f5f1bca1ec6cb204bfe5fea0230845e83014186675cb6706f9d51167fb0f14cd3f8fcfb0065093f62b10a15f7d9a6c8d9824a468603fdcb7a2eb5770705898cf9ef37aade532a7964642ecd705a74794b794b76e54de0243274f97430b26624c44694fbde3289ed81a160e0754ab9f56f324c69f22dfd92b54fbc27f27948af15958adfbc607d68d6ed0faca394c424ccee57c12d8573d2f3883a8a0ba14e3eec02ac1c61dee6b675b6c0d16e221c3777f45ad4efd90dcde01d26cc6f32f7ce3ce0b4d4951d4b94a19aa097341aff2acaec5b4322ec672fdfeb292941057125d00afcf1a904e31f9ec0fb9e650177dba5005d26835be2cf4f08f2beeff301c06d05035d0a9ec3afacc71dff22813595c0b96747b820d785398d6fca544b100af624af4c3c6339a69d7ffaf4c2af8301654d78e3f87f31688355c0f398317b2d87d803bd87ee3656c5a7c80f0561ec8606df7c465ea7bcccf4f94147add808f24629644be11c0ba4823f16e8c19e0090f0ff80457fd3c283b3da95ee8e9cb62c28c51a05ca6b1b03f84c3737de2d951d17cd8321dfdf54fa41c6ef19abe98df0f5ef80387790e8df000f6fd6dc71ea566c07940dec2039c7fca4a08d08601971836916c6ad5193be07a88506ba58e06d4b4d9b60c622546dc45cca64df935b71c26dcf4886d6fa811944dbc4e23db93356409fb39f162c1e1eb55fbf38e670d5e329d84542d3dfcdc341a99f5d07c4b50977a141e45c3b121aa084f23ebbff980c4b96ae8db2a8d6fde459781aa6d8a5e99aa3900daf137c81ca37a4bf10e9857526d3978be085be265393f98cb075795740a50d6db532a658ebbebe4c13624bc7bdada0dbf4b0f279e0c151992f7271c726aee20f9188a5c3954623583c6b0e6623ec90d5cd3fdec4e1001646e27664002cb13c1c0dfd66807f6e703e744f6bb5a60b9cbde8bf32403a74edce14f52af305b47e281bfbeeb0758f8c625bed5c5a0d27ee8e0065ceeadd76b0010d226206f0b66db13d17ae8bcaf586180e3dcd1e2e0a084b6bc987ac829bbff18c3be7f8b4b9c5d4339809e0ad9a00d4d3dd26fdf44a32819a54abf846bb9b560d81391c25c1f929afa37253d28074e8fdaf62f0e3447ca3ed9b51203f676c1244b5b86955c365ddaa345cfcaff3d629505572a484cff5221933d68e4a52130b8bb7badaf9ca29de1dc8817868c93e54b09f557fe14e40083c0955294df5bd91f52ba469c8d8a9879a99ac7b12e63e6bcae7f965fbf1b63d892a8649ab1d6b08ce711f7127dceef54e6670388c81b5a8b8583d5e7c5245ce4dd40a83439afeb4f14693367de14f1a655d54254d06d51cd23a2fa57b6ffdf371cf6b828ee483b1b1d6d21079e8450dd6f908b23c9cbd6011fe3d940b24c0420a208d6924e2d920f92c894a96eb72085fd9b3cf136f84d69643c31a48d1e03dda550268885891d26bf09b469ced01ebfbc9eb5bbea545af4d01bf5f1071661840480439c6e5babe8e080e41aaf8812f1deb8001f3b7672b6fc85640ecb123bc2304b563728e6235ccbe782d85fc626fe1e0f4d77b34851a8c60cdd11172472da3b9325bfe288ac8342f6c710a